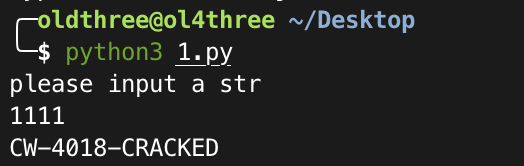
crackme-系列之-crackme1
首先打开程序进行查看
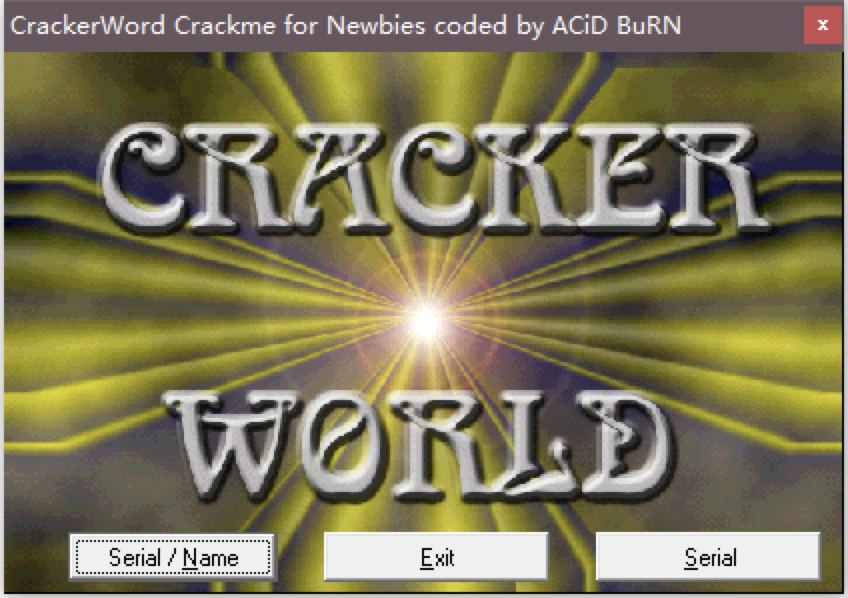
发现无壳
逻辑分析
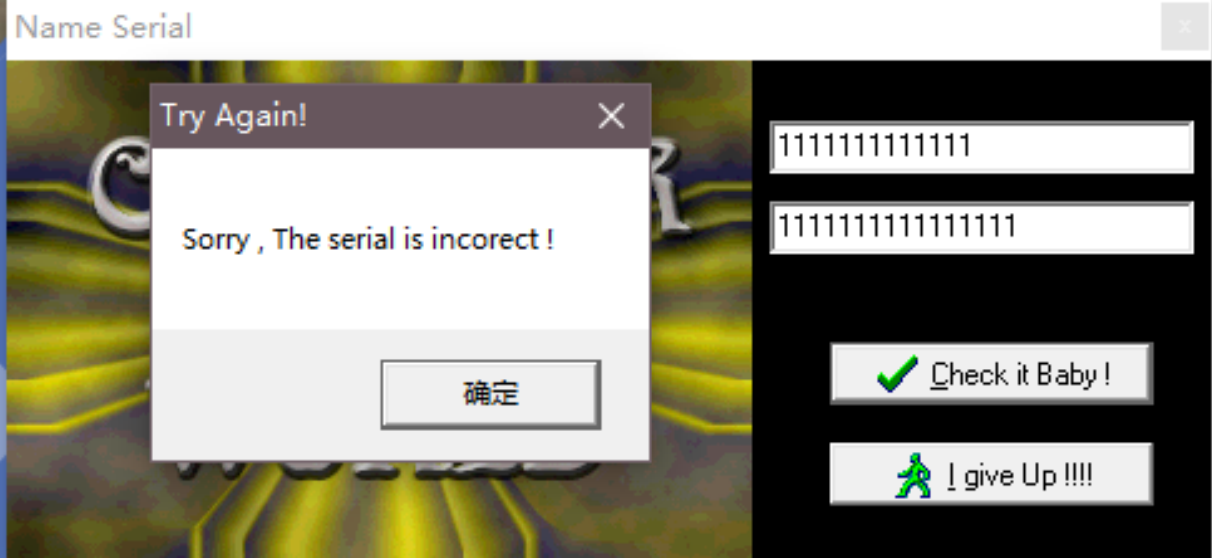
账户密码认证 直接仍进去OD进行分析 搜索关键字
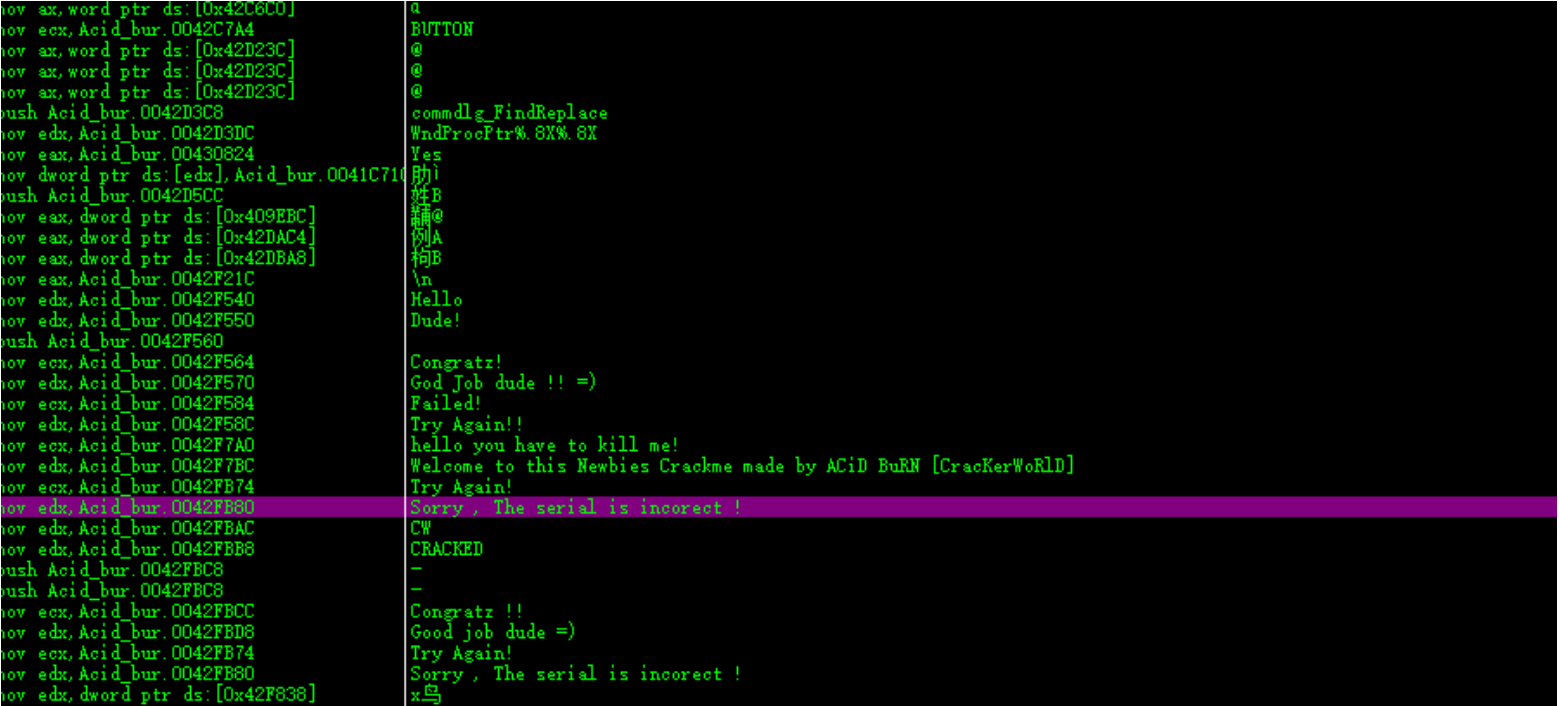
在函数⼊⼝处下断点然后运⾏跟踪
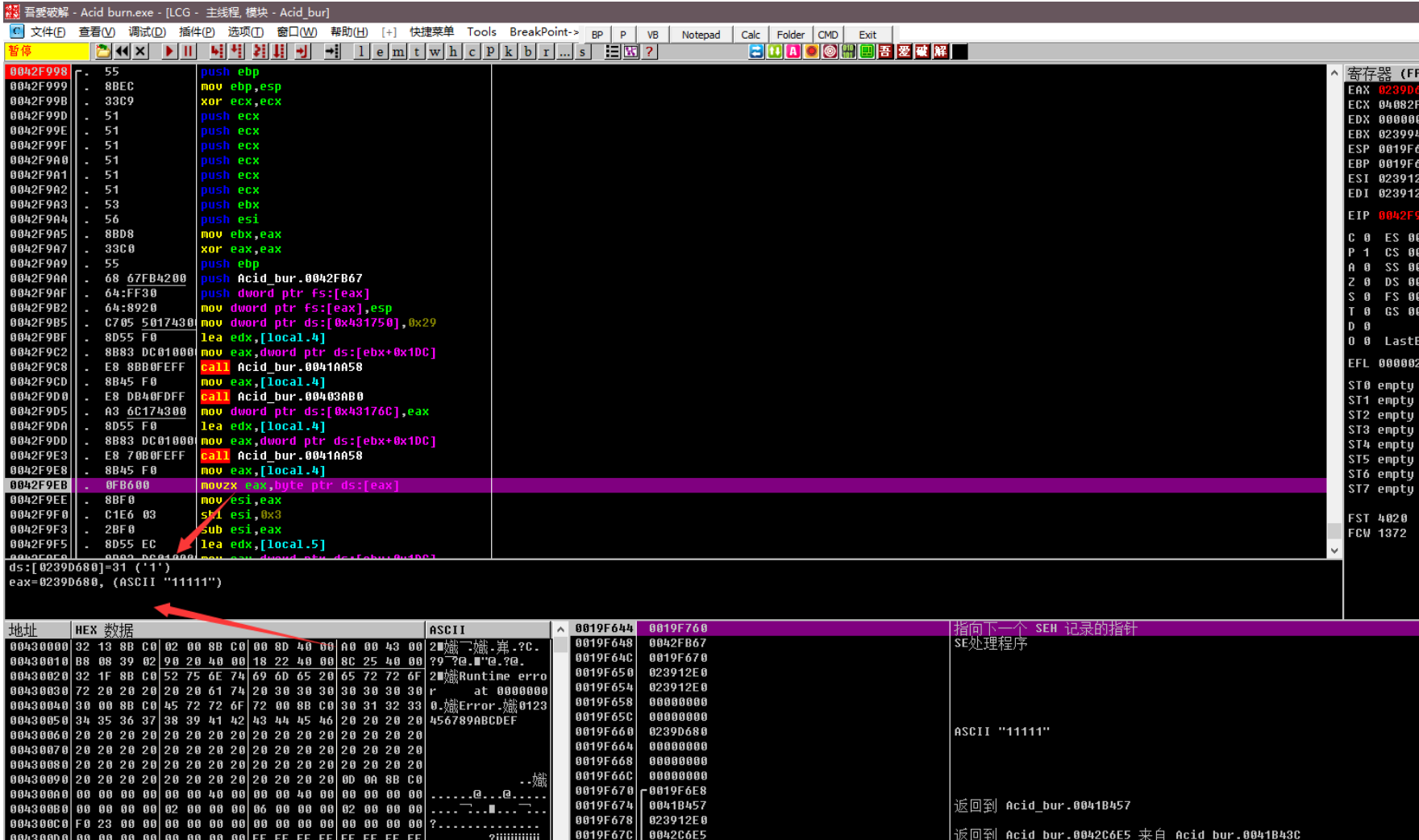
输⼊11111 11111

发现关键call 和对比进入分析
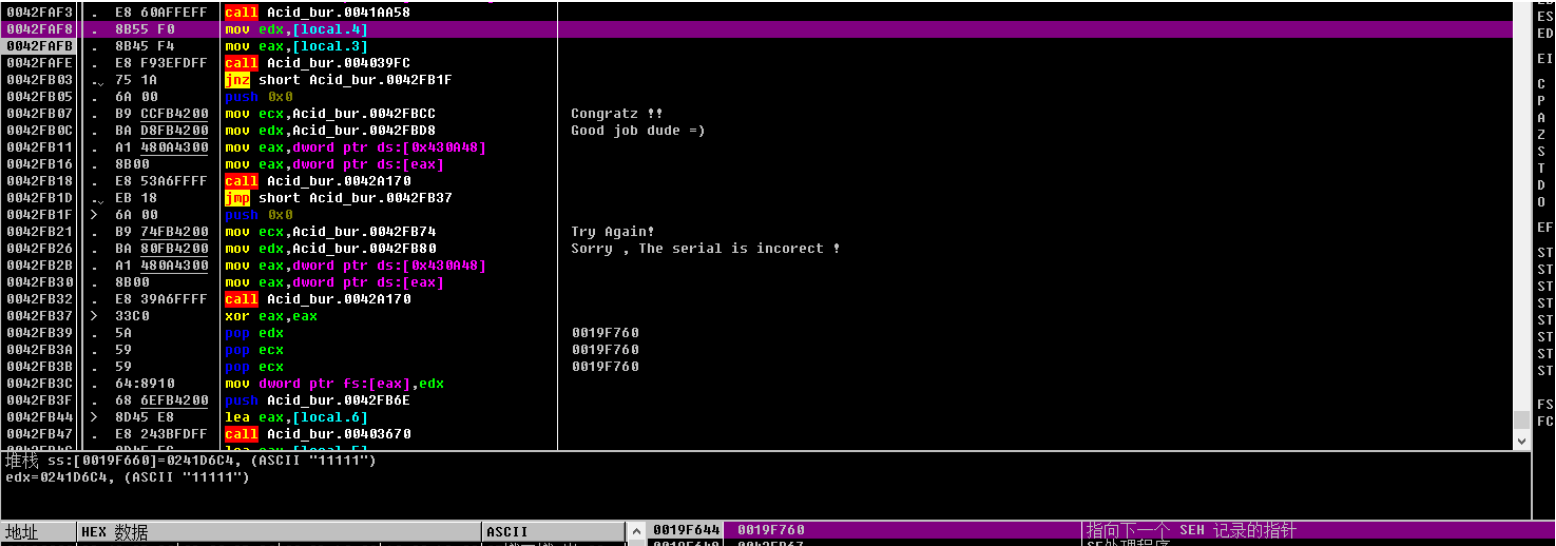
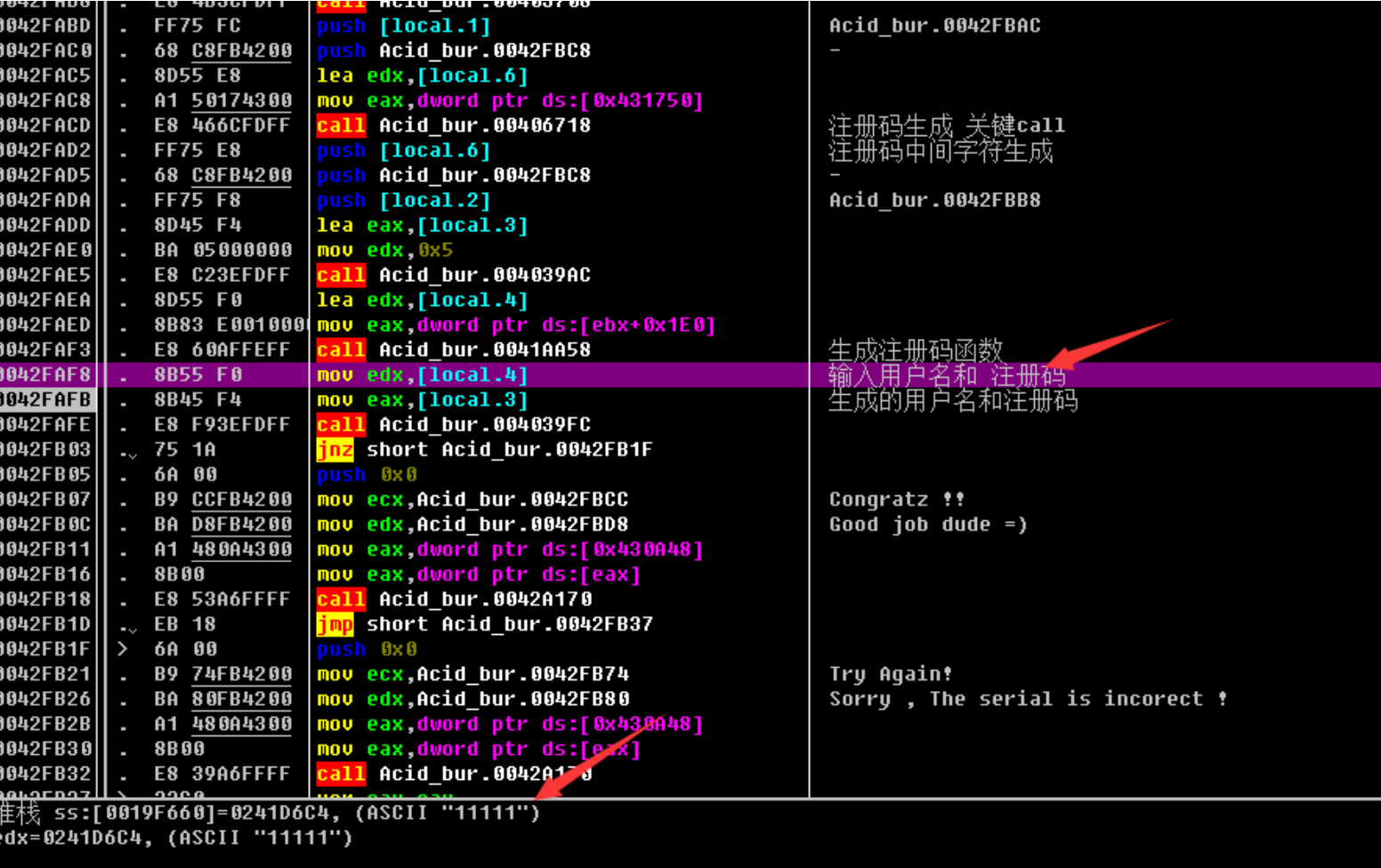
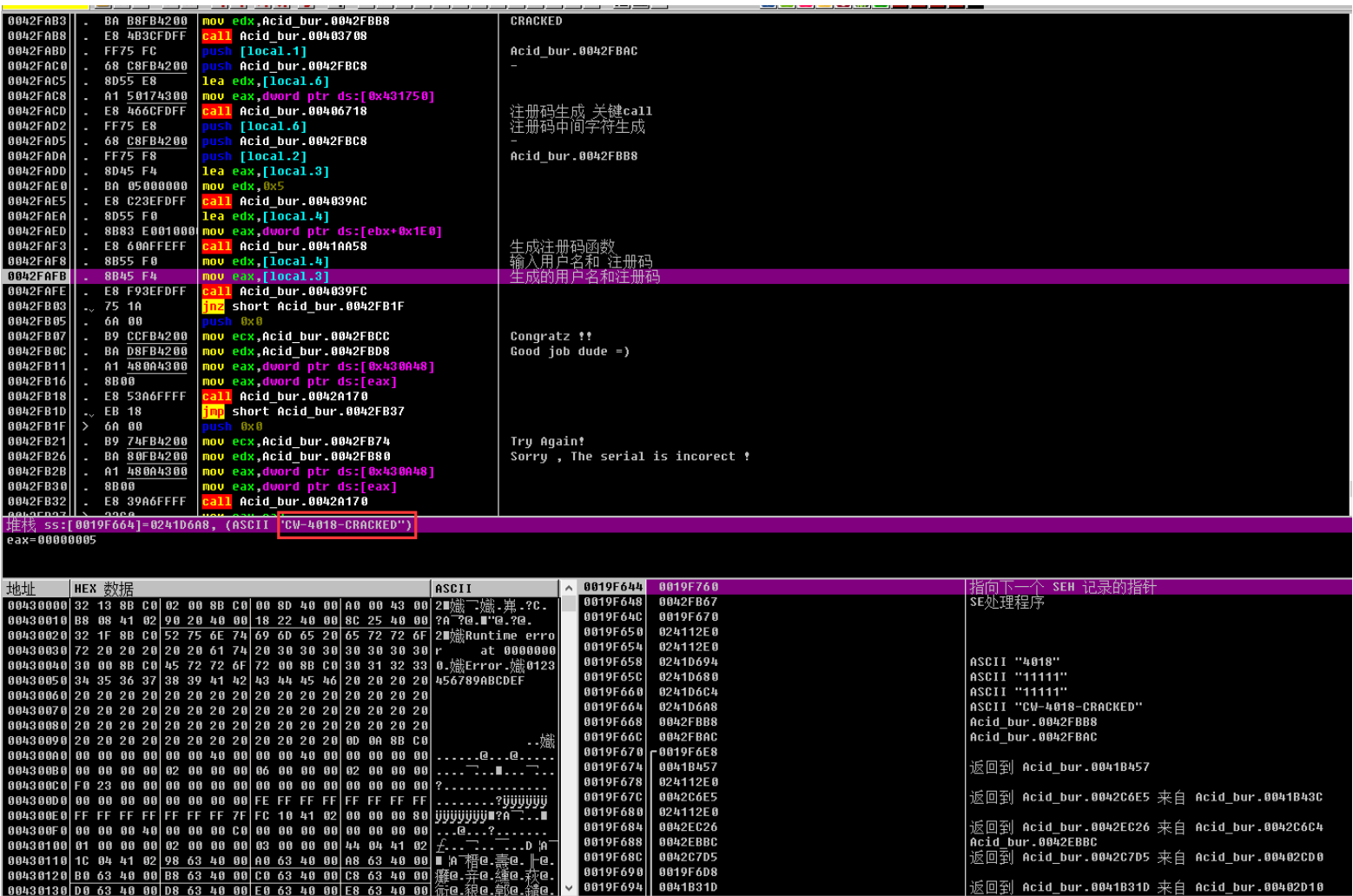
⽤户 11111
堆栈 ss:[0019F664]=0241D6A8, (ASCII “CW-4018-CRACKED”)
eax=00000005
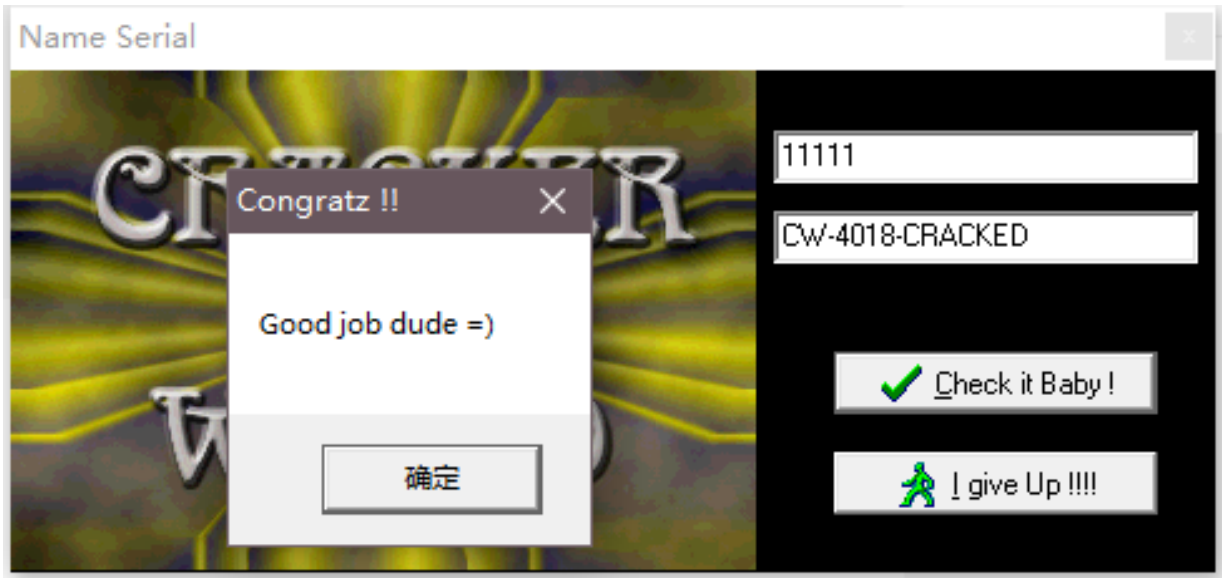
输⼊后成功破解
对算法进行相应的破解
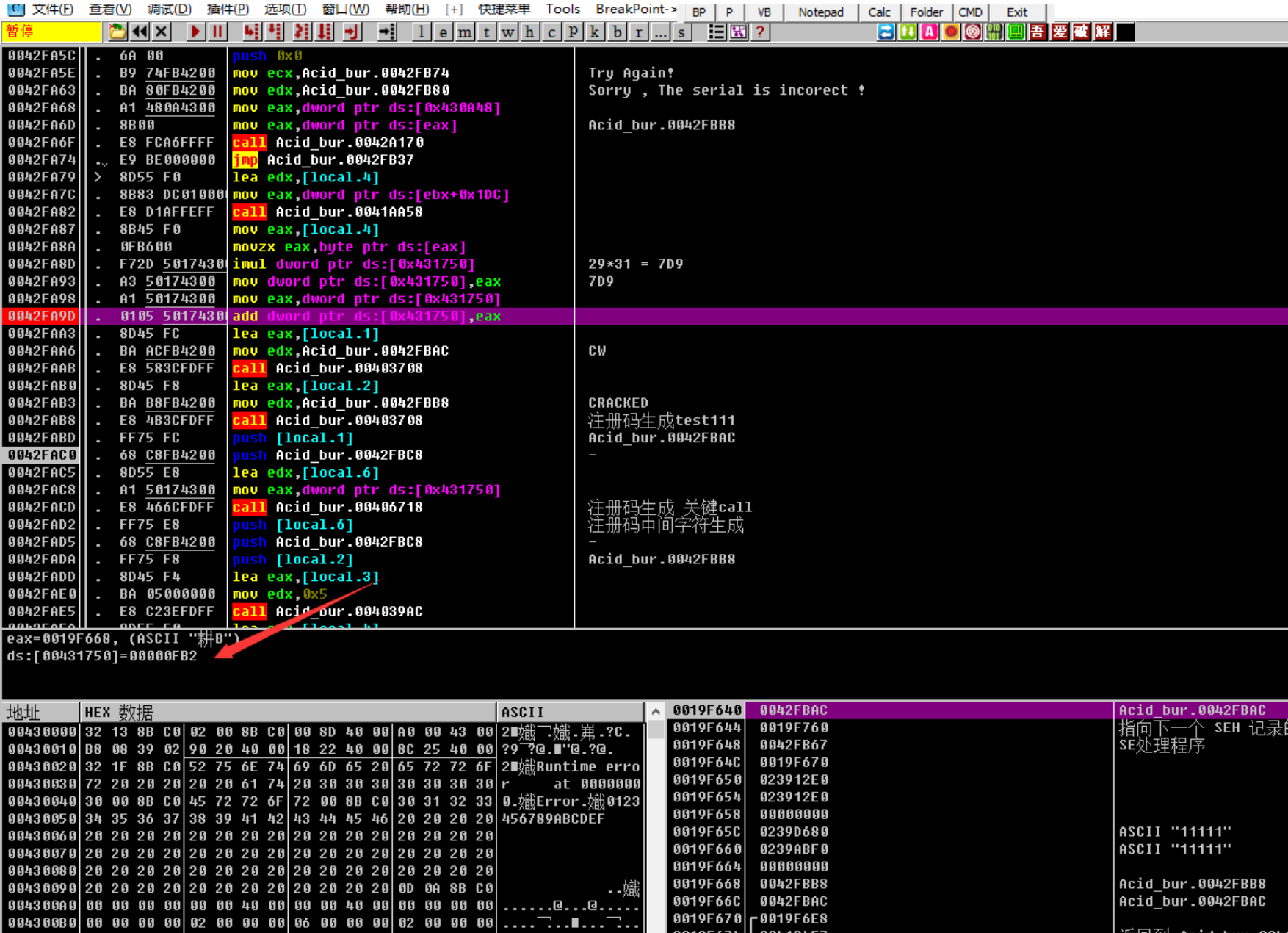
下断点 输⼊ 11111 22222
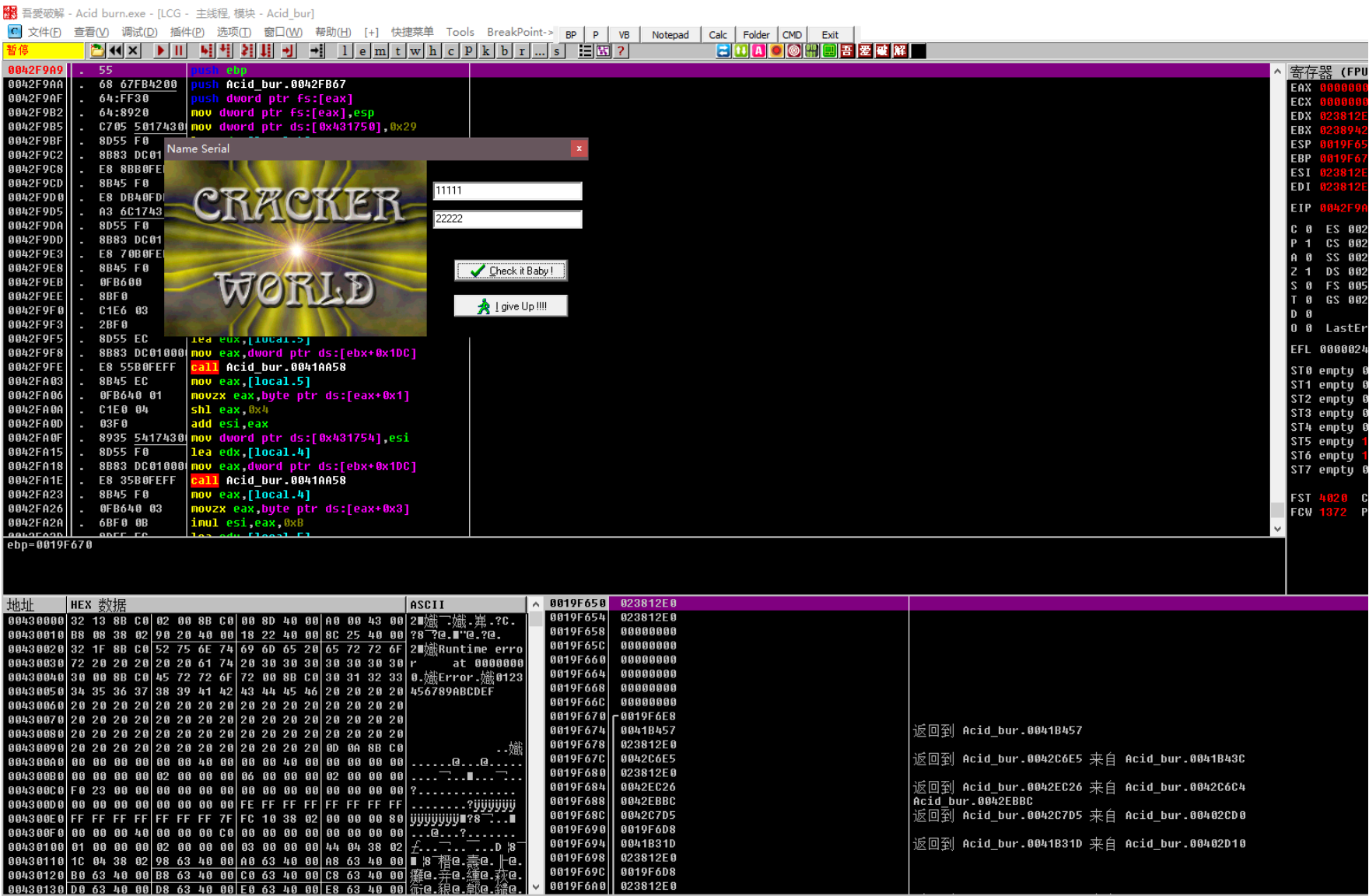
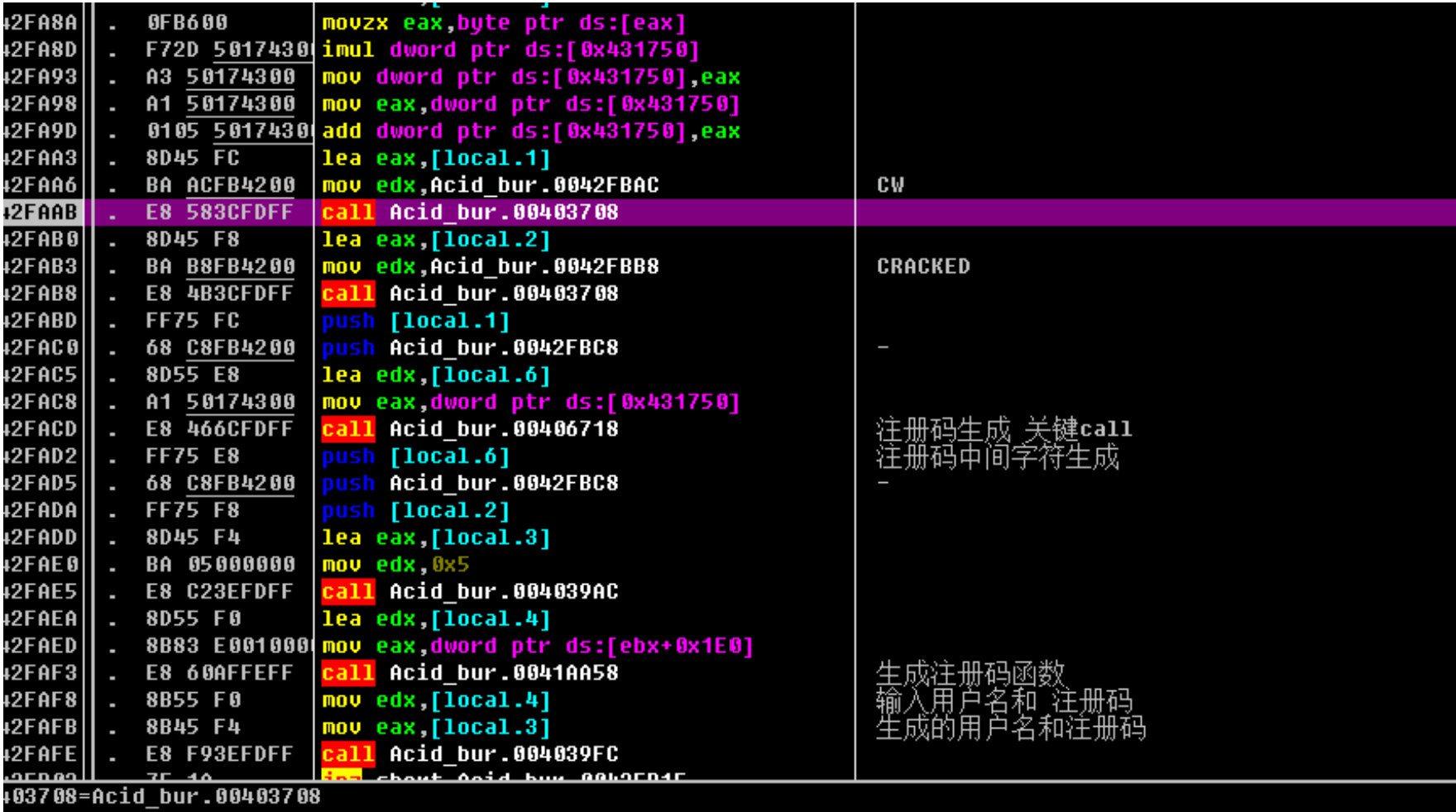
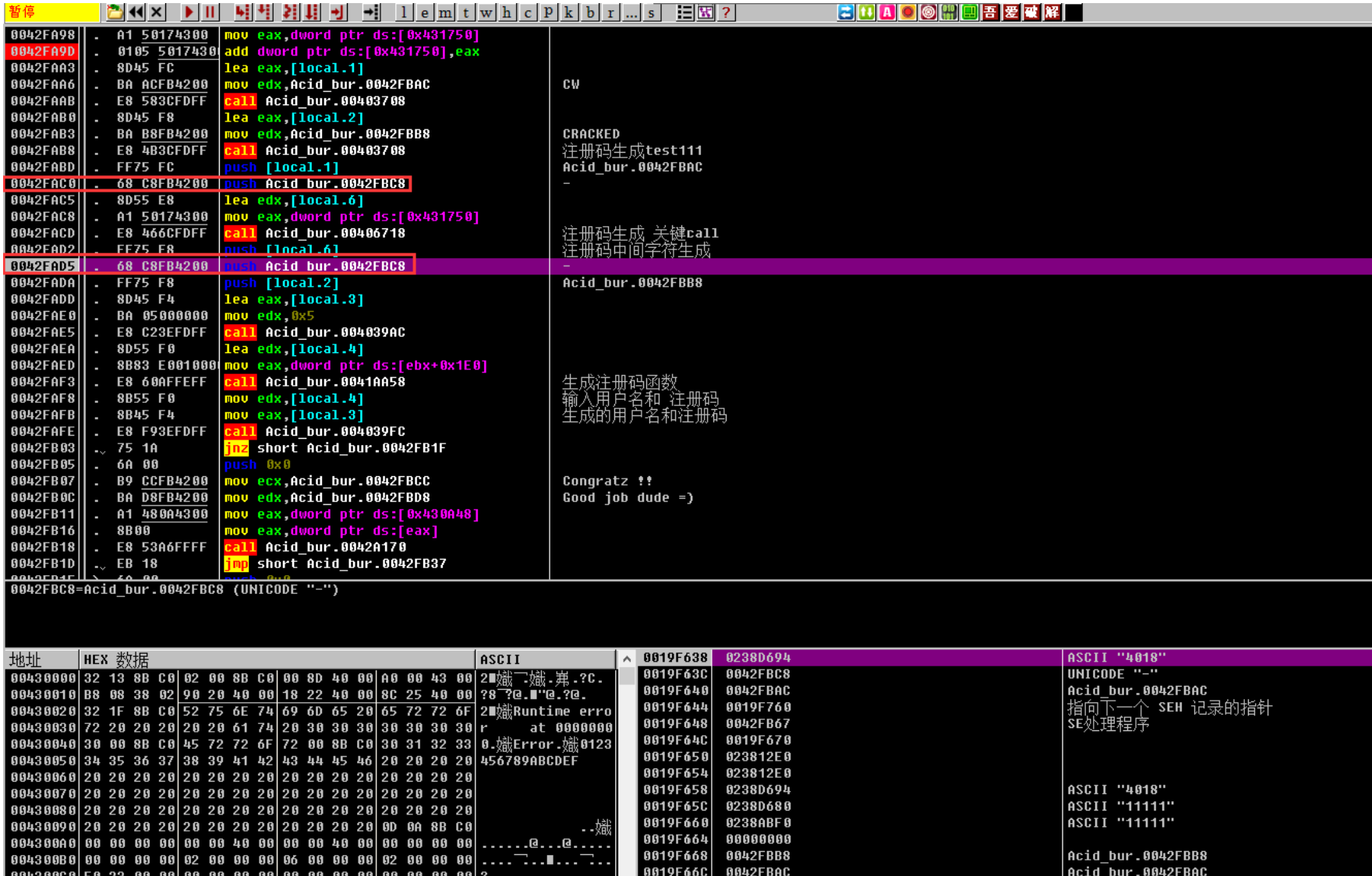
发现有两次-的拼接
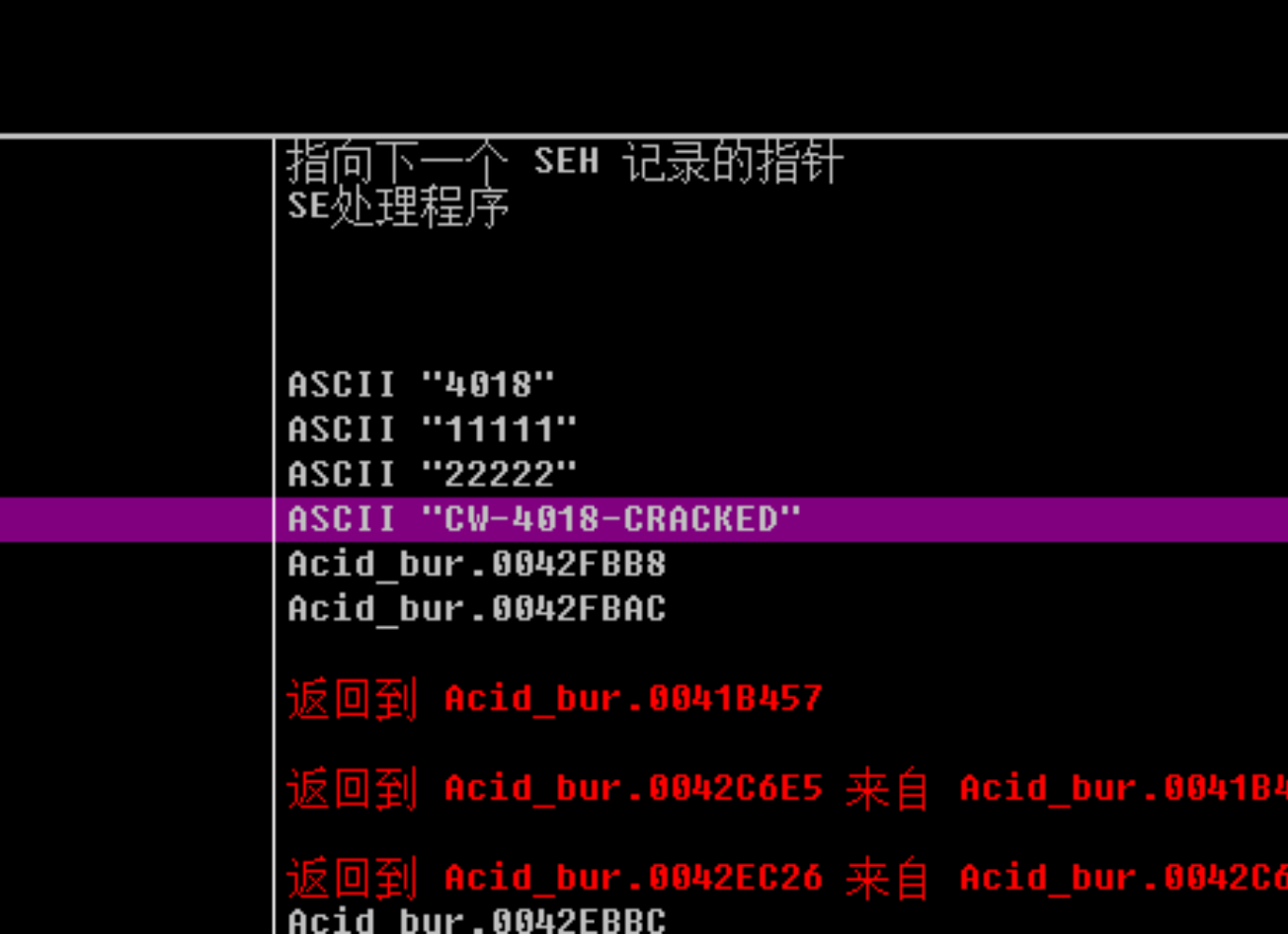
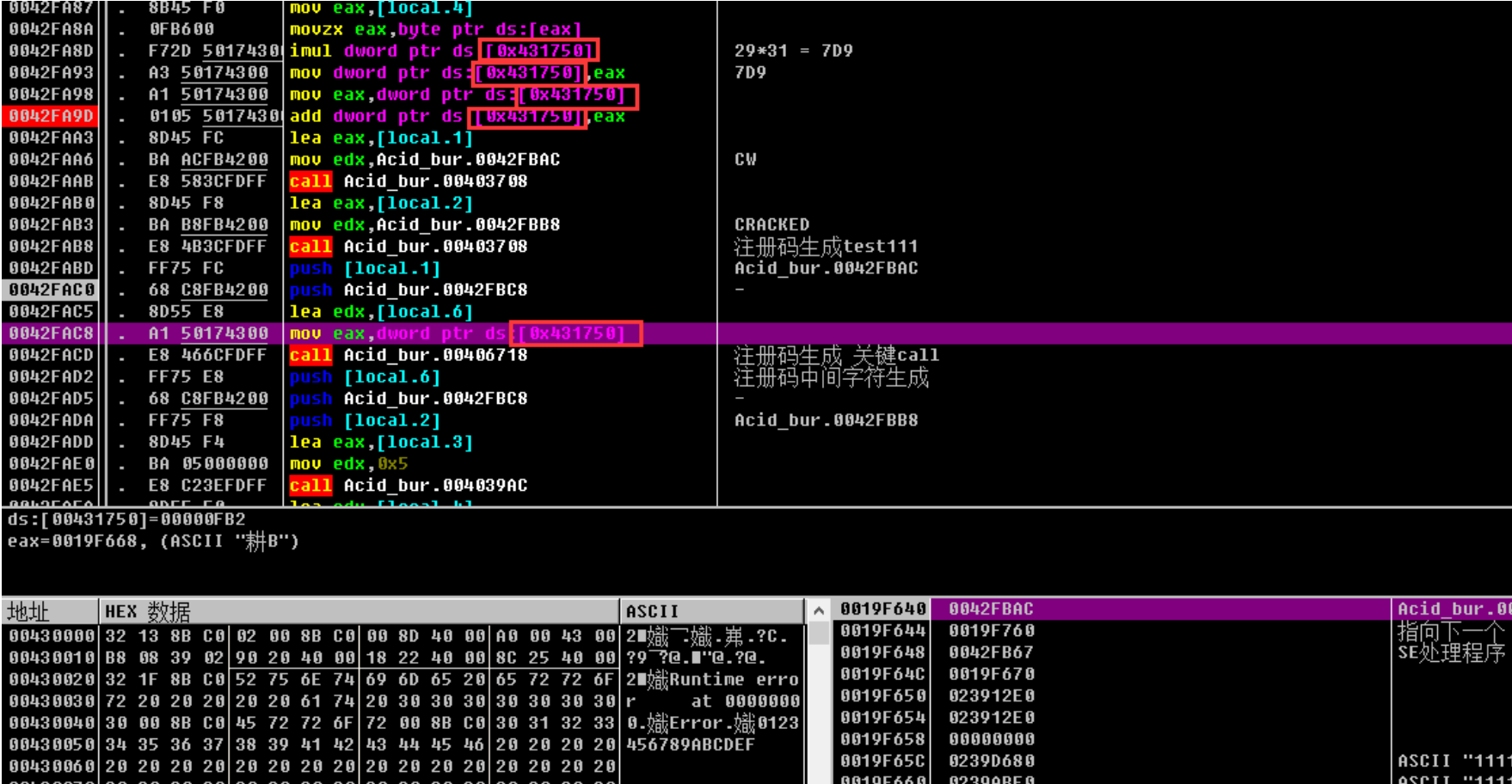
CW-xxxx-CRACKED
这⾥为取第⼀⼀位 ascii码值的16进制 31 x 0x29
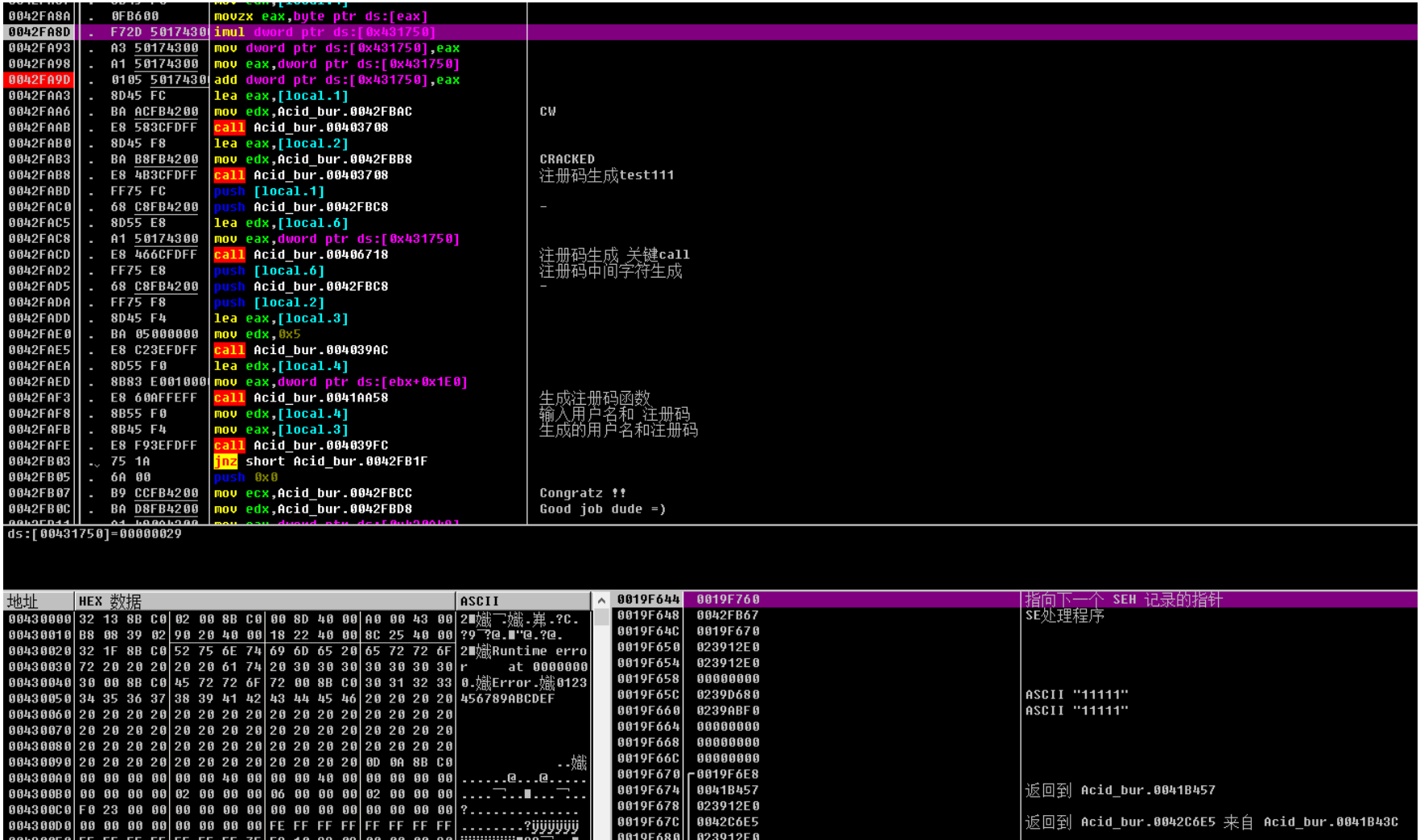
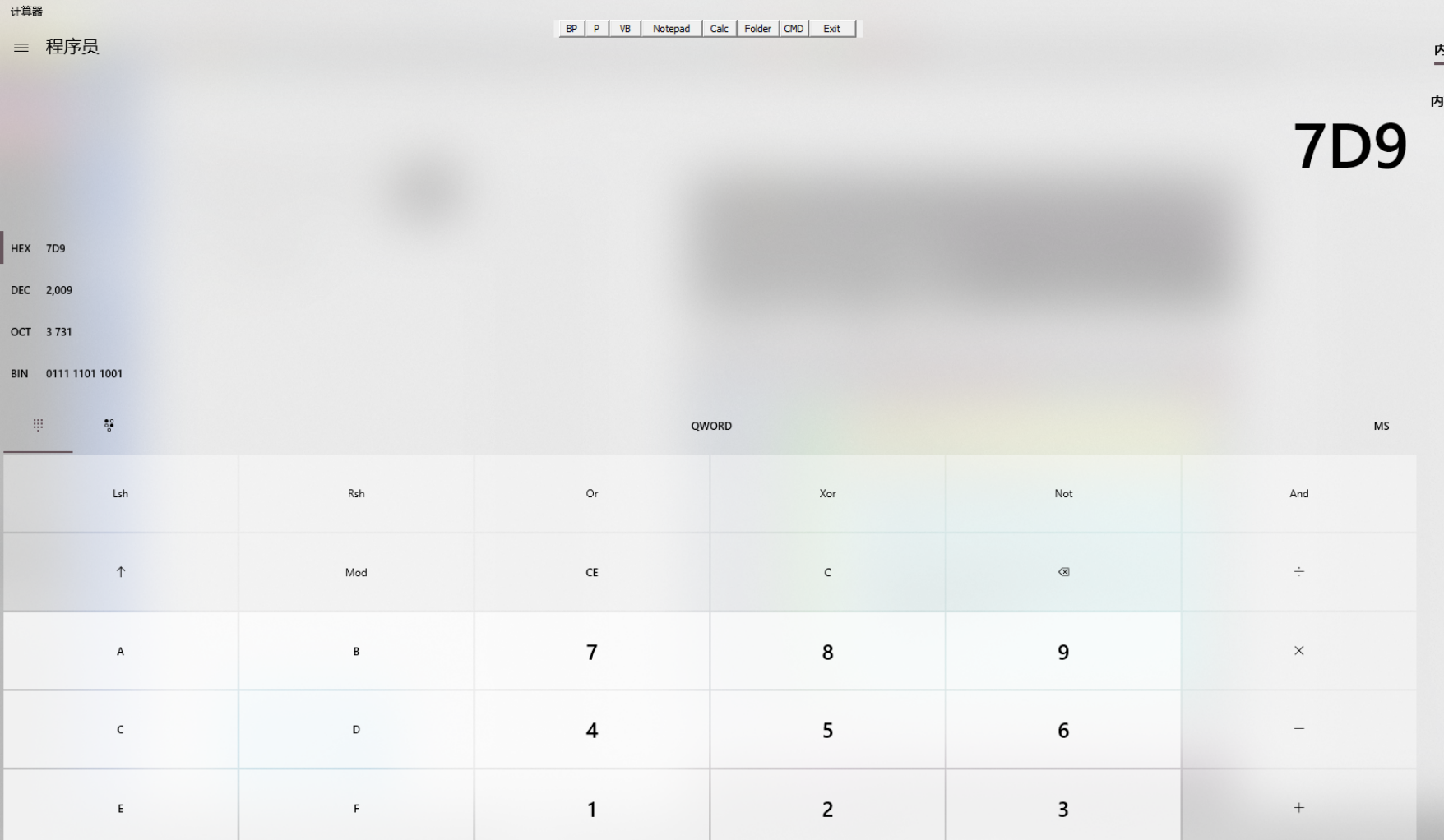
相乘之后为 0x7d9
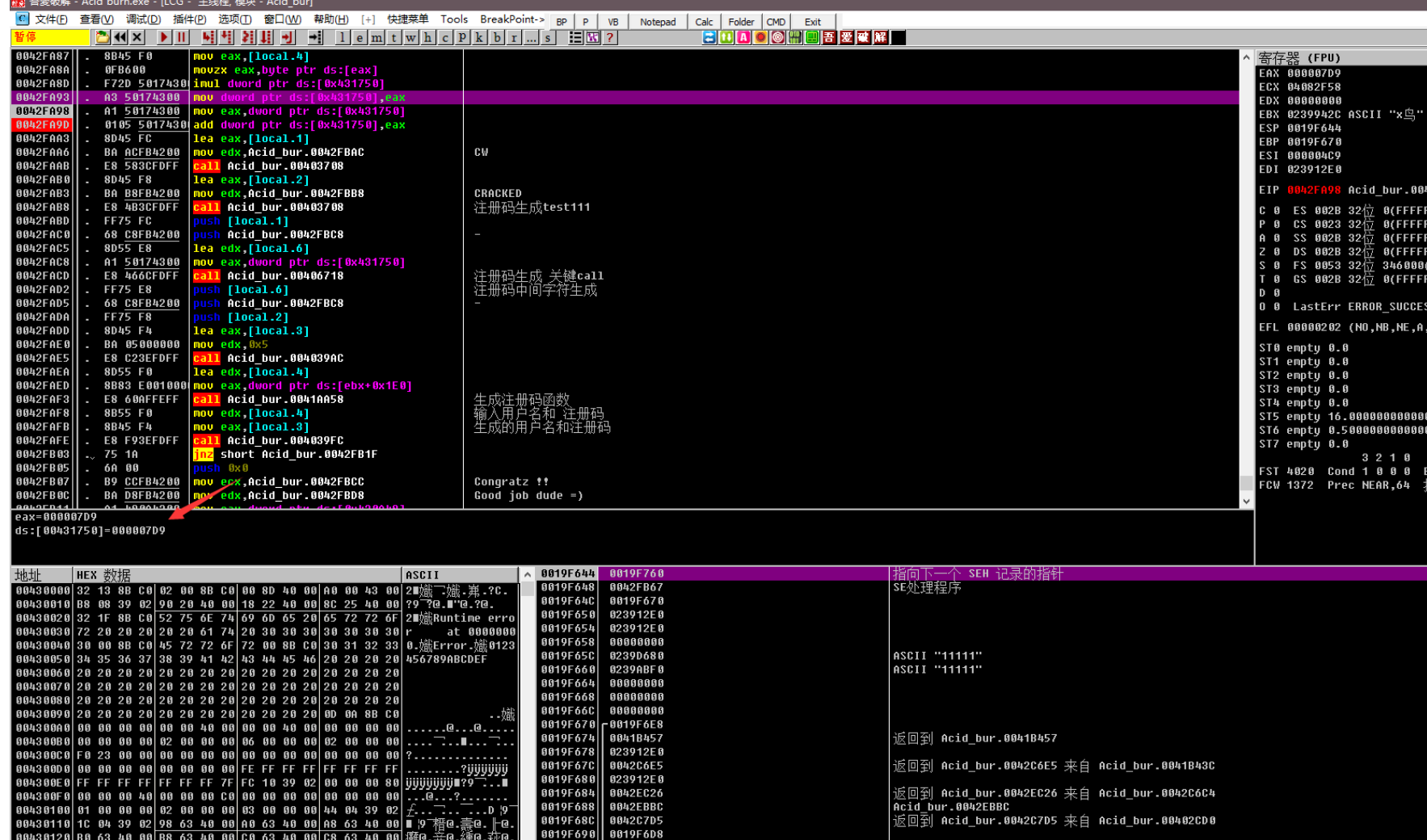
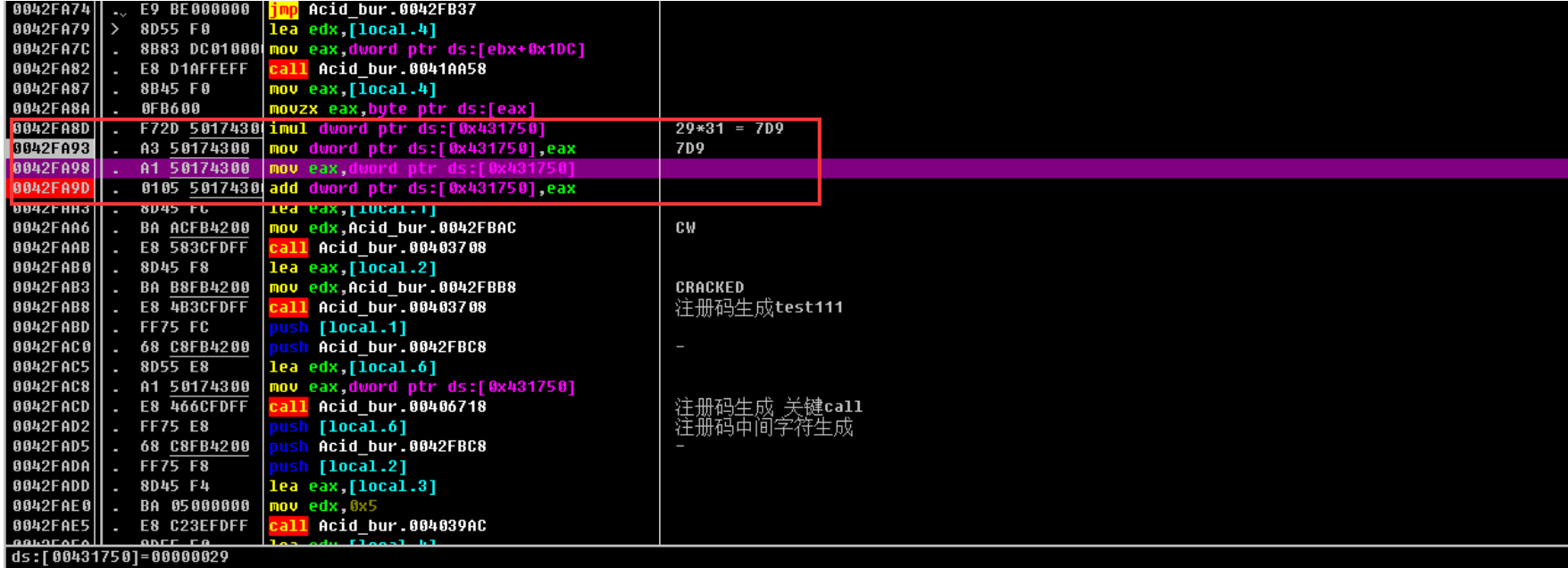
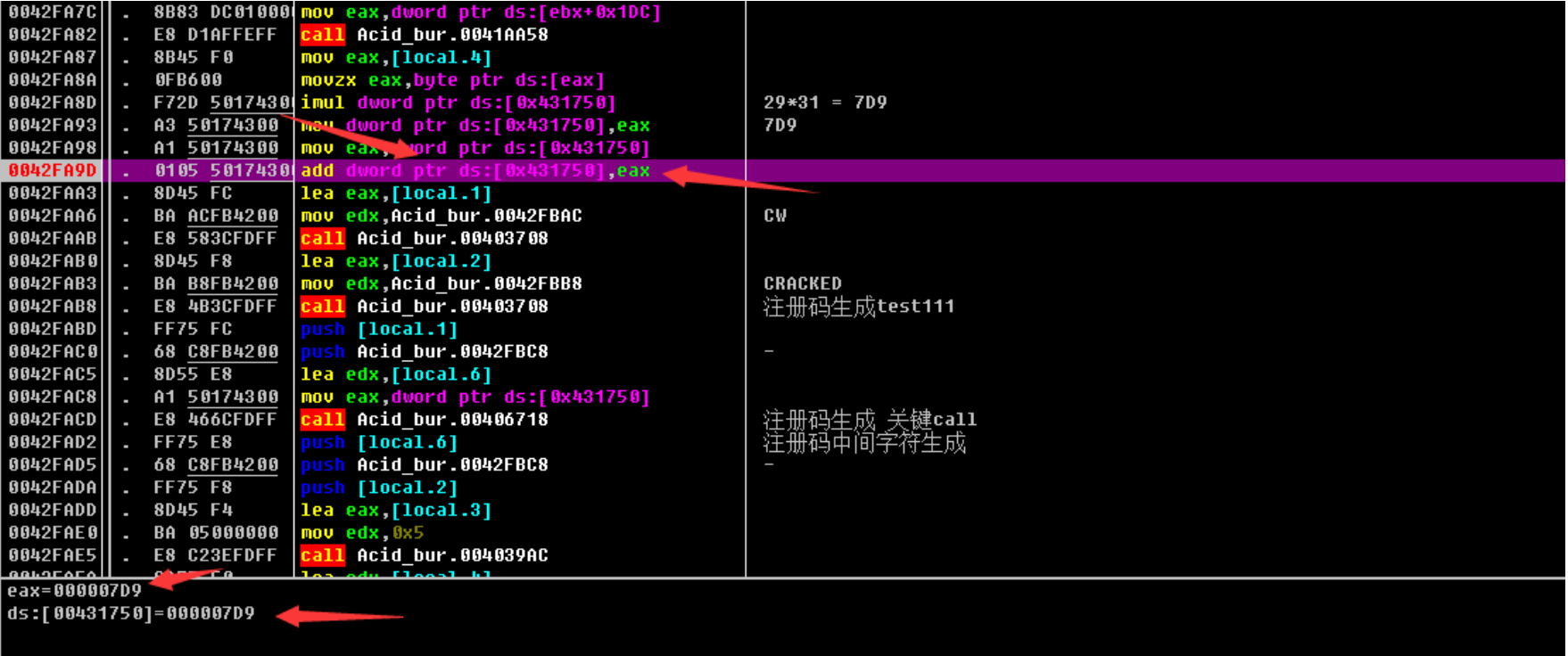
⾃身x2
之后转10进制即可
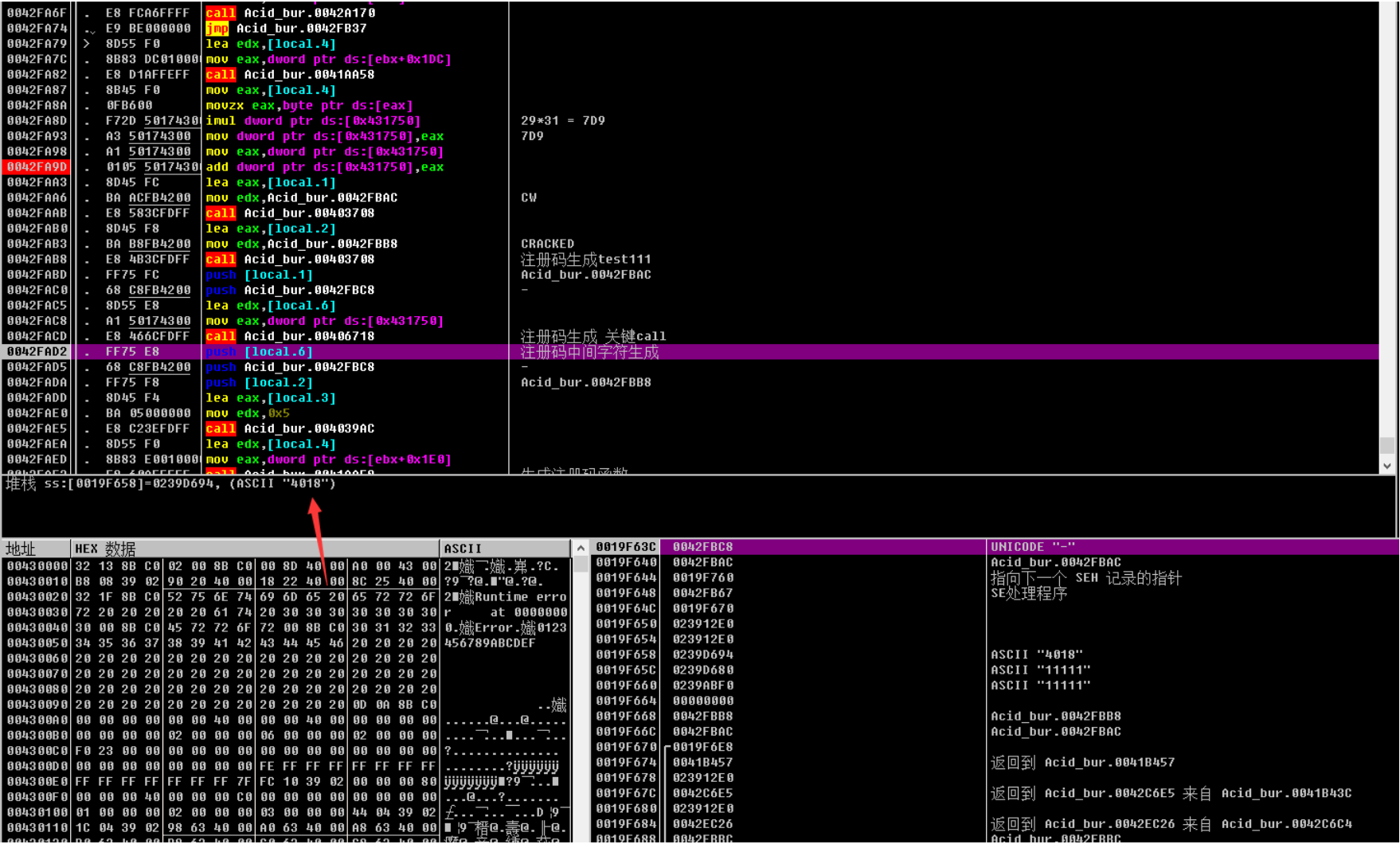
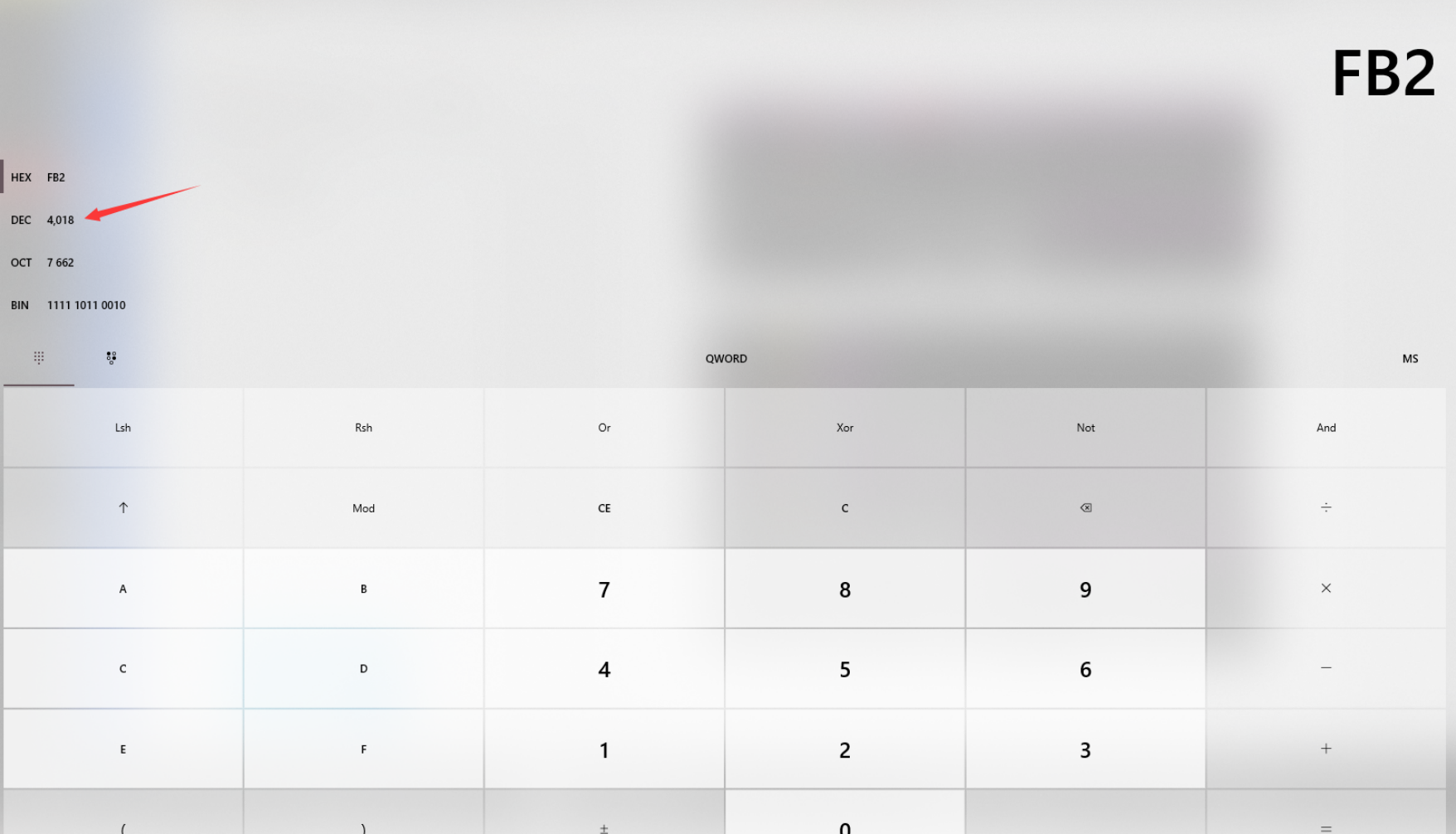
接下来是字符拼接
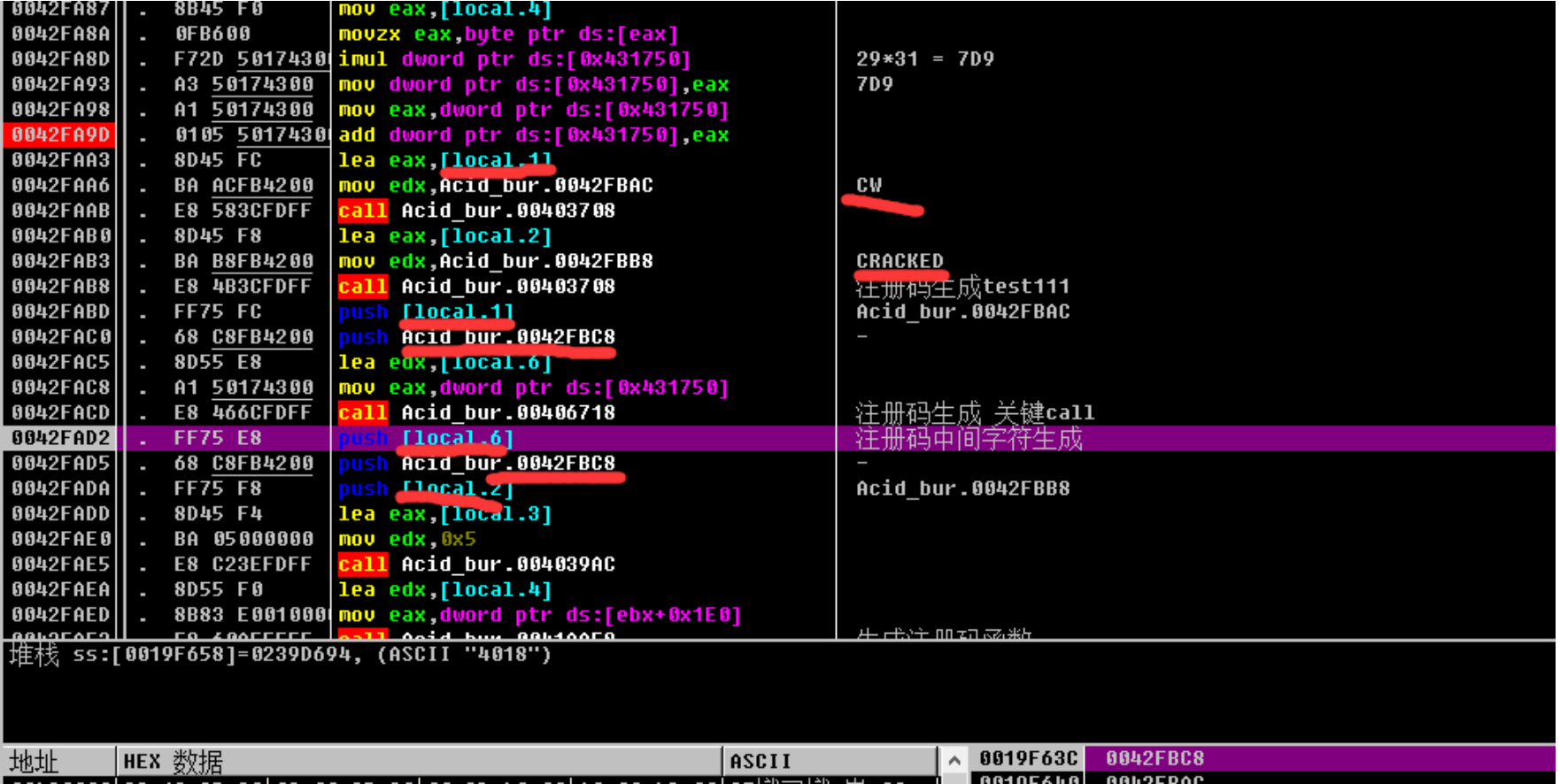
根据push关系可以推断出此处注册码为:
CW-4018-CRACKED
#####
算法脚本如下:
c = input("please input a str\n") |